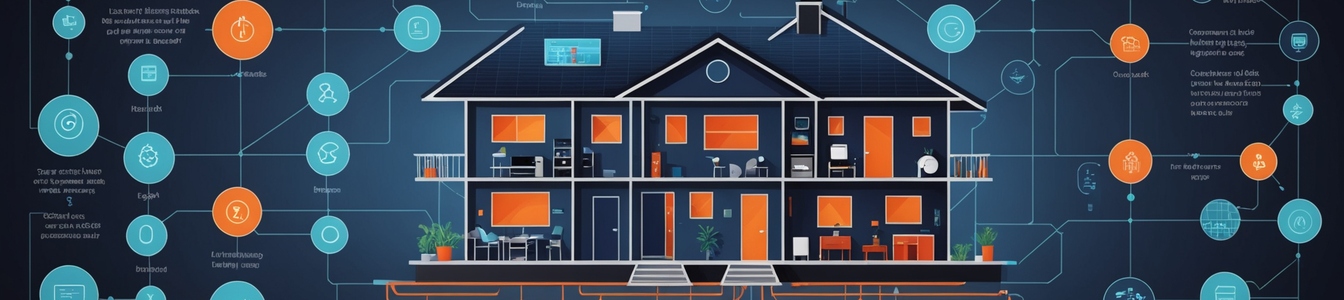
The narrative at CES has decisively shifted. No longer just a parade of singular, clever gadgets, CES 2026 marks the mainstream arrival of the holistic, branded smart home ecosystem. Major manufacturers are no longer selling just a TV or a vacuum; they are selling an integrated, AI-orchestrated living experience. This paradigm, showcased by giants like Hisense, UGREEN, and Changhong, promises seamless convenience but introduces a fundamentally new and distributed risk model for cybersecurity professionals. The attack surface is no longer a collection of points; it's a living, breathing network with a single, often opaque, intelligence.
The Rise of the 'Full-Scenario' Ecosystem
Hisense's presentation of a 'Full-Scenario Smart Home Ecosystem' encapsulates the trend. It's a vision where entertainment systems, kitchen appliances, climate control, and lighting are not just connected to the internet, but are deeply interlinked through a proprietary or consortium-based interoperability layer. Actions cascade: a movie ending triggers lights to brighten and the thermostat to adjust. Similarly, Changhong is pushing 'AI-Powered Smart Home Solutions' that leverage machine learning to predict and automate user behavior across devices. The value proposition is powerful: a home that anticipates and serves. For security, however, this creates a web of trust where a vulnerability in a less-secure device, like a smart bulb, can become a bridgehead to access more sensitive systems, like security cameras or network storage, all under the veil of legitimate, intra-ecosystem communication.
The AI Hub: UGREEN's Centralized Risk Model
UGREEN's strategy highlights a critical architectural shift and its attendant risks. The company debuted a new smart ecosystem led by an 'AI NAS' (Network-Attached Storage). This positions a powerful, data-rich device as the central brain of the home. This AI NAS doesn't just store data from UGREEN's security cameras and sensors (part of its new security platform); it analyzes it, makes decisions, and coordinates actions across the ecosystem. This centralization creates a high-value target of immense potency. A compromise of the AI NAS could lead to a total loss of privacy (access to all stored personal media, documents, and video feeds), enable pervasive surveillance, and allow an attacker to issue malicious commands to every connected device. The 'smart home security platform' becomes, paradoxically, a single point of catastrophic failure. The AI models themselves become an attack vector—could they be poisoned or manipulated to create unsafe conditions or false alerts?
The Invisible Handshake and the Death of the Perimeter
The core security challenge lies in the 'invisible handshake'—the automated, behind-the-scenes authentication and communication protocols that bind these ecosystem devices. Unlike traditional IT where firewalls guard boundaries, these devices implicitly trust each other by virtue of sharing a brand, a hub, or a common standard like Matter. This trust is often established during simple setup processes (e.g., QR code scanning) and is rarely questioned again. An attacker who breaches one device gains a trusted position within the ecosystem, enabling lateral movement that is extremely difficult to detect with conventional network security tools. The perimeter is everywhere and nowhere.
Implications for Cybersecurity Strategy
This evolution demands a corresponding shift in defensive postures:
- Supply Chain & Firmware Integrity: Security assessments must extend to every device in the ecosystem, demanding robust firmware update mechanisms and hardware-based root of trust from all vendors, not just the hub manufacturer.
- Protocol & Standard Security: The security of the interoperability protocols (whether proprietary or open) must be scrutinized. Encryption for data-in-transit is table stakes; attention must now also be paid to authentication robustness and the potential for protocol-level exploits.
- AI Security Governance: For ecosystems driven by AI hubs, organizations need frameworks to assess the security of the machine learning models—guarding against adversarial attacks, data leakage, and ensuring the AI's decision-making logic cannot be hijacked.
- Network Segmentation for IoT: The classic advice gains new urgency. IoT ecosystems must be rigorously segmented from primary corporate or personal IT networks. However, this becomes more complex when the ecosystem's hub (like an AI NAS) also stores sensitive personal or work data.
- Vendor Risk Management: Choosing an ecosystem is a major cybersecurity decision. Professionals must evaluate the vendor's security maturity, transparency, patch commitment, and history, treating them as a critical software vendor.
The convenience of CES 2026's integrated visions is undeniable. Yet, for the cybersecurity community, these ecosystems represent a consolidation of risk into attractive, high-value targets. Defending them requires moving beyond device-level thinking to ecosystem-level security architecture, questioning the very trust models that make them convenient. The invisible handshake must become visible, auditable, and secure.
Comentarios 0
Comentando como:
¡Únete a la conversación!
Sé el primero en compartir tu opinión sobre este artículo.
¡Inicia la conversación!
Sé el primero en comentar este artículo.