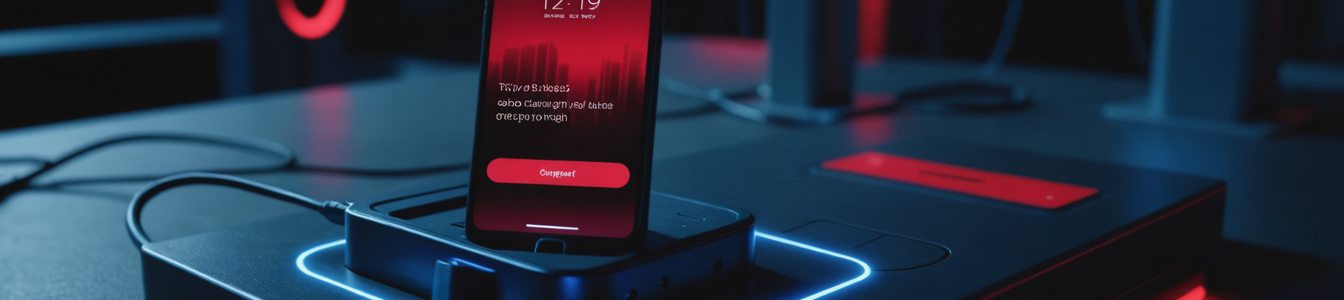
The cybersecurity landscape is witnessing a concerning evolution in mobile threats as public charging stations become increasingly weaponized. While 'juice jacking' - the practice of stealing data or installing malware through public USB ports - has been known for years, security researchers are now warning about a more sophisticated threat called 'choicejacking' that represents the next generation of charging station attacks.
Choicejacking differs from traditional juice jacking in its psychological manipulation component. Rather than simply exploiting the physical USB connection, attackers create interfaces that deliberately guide users toward making dangerous choices. These may include fake system update prompts, misleading permission requests, or seemingly legitimate app installations that appear while the device is charging.
Technical analysis reveals that modern choicejacking attacks often involve:
- Custom firmware on charging stations that mimics device interfaces
- Social engineering elements that create false urgency
- Multi-stage attacks that begin with charging but escalate to full device compromise
- Bluetooth or WiFi-based follow-up attacks after initial USB connection
One emerging solution comes from innovative accessories like USB-C lanyards that combine charging functionality with wearable convenience. These devices allow users to carry their own trusted power source, completely bypassing public charging stations. Security experts recommend these as part of a broader defense strategy that includes:
- Always using AC power adapters instead of direct USB connections
- Carrying portable power banks for emergency charging
- Disabling data transfer during any public charging session
- Using USB condoms (data blockers) when public charging is unavoidable
As public charging infrastructure becomes more sophisticated, so too do the threats against mobile devices. Choicejacking represents a particularly dangerous evolution because it exploits human psychology rather than just technical vulnerabilities. Security professionals should educate users about these risks while organizations need to reconsider the security of public charging solutions in corporate environments.
Comentarios 0
Comentando como:
¡Únete a la conversación!
Sé el primero en compartir tu opinión sobre este artículo.
¡Inicia la conversación!
Sé el primero en comentar este artículo.