A persistent and psychologically effective phishing campaign is exploiting the global Netflix user base, using fabricated payment failure notifications and account cancellation threats to steal login credentials and financial data. Security researchers have documented a surge in these attacks, particularly targeting German-speaking audiences, though the templates and tactics suggest a scalable, multilingual operation.
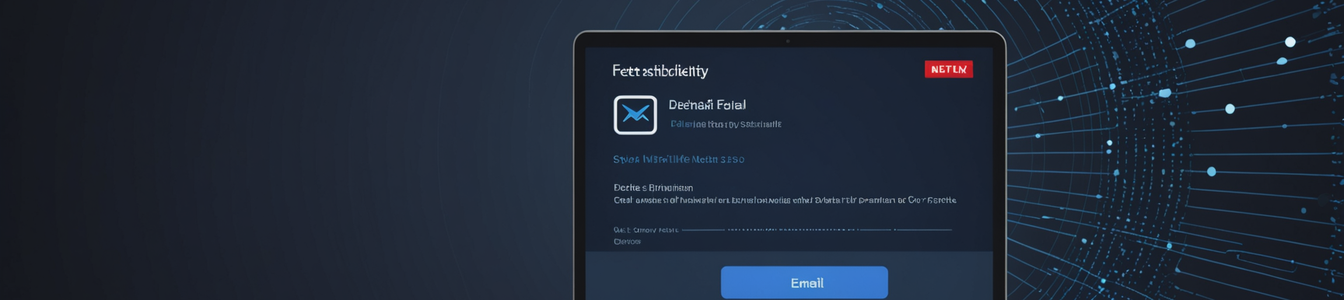
The attack vector begins with a deceptive email, often with a subject line such as "Information regarding your account" or "Monthly payment failed." The message body expertly replicates Netflix's corporate design language, including official logos, fonts, and color schemes. The core social engineering hook is the creation of urgent, negative consequences—typically, the imminent suspension of the service due to a purported issue with the user's payment method. This triggers an anxiety response, clouding judgment and prompting hasty action.
The email instructs the recipient to click a link to "update payment details" or "verify account information." This link, however, redirects to a phishing domain meticulously crafted to resemble the genuine Netflix login page. These fraudulent sites often use URLs that are slight misspellings of the legitimate domain (e.g., 'netfflix.com') or employ subdomains designed to look authentic. Once a victim enters their email and password, the credentials are captured by the attackers in real-time. In some advanced iterations, the phishing page may even redirect the user to the real Netflix site after stealing their data, adding a layer of believability to the scam.
Technical and Psychological Analysis
From a technical standpoint, the campaign is not particularly novel, but its execution is polished. The phishing kits used are readily available on cybercriminal forums, allowing low-skilled threat actors to deploy them. The true sophistication lies in the operational security (OpSec) and the psychological profiling. The attackers are likely leveraging data from previous breaches to target active Netflix subscribers, increasing the hit rate. The choice to focus on a payment failure scenario is strategically timed; during holiday periods, users are more likely to have altered spending patterns, making such an alert seem plausible.
For the cybersecurity community, this campaign underscores several enduring truths. First, brand impersonation remains one of the most profitable attack vectors due to the inherent trust users place in major services. Second, attacks that invoke fear and urgency (FUD - Fear, Uncertainty, and Doubt) bypass rational security thinking. Third, the global nature of streaming services provides a vast, homogeneous target pool for phishers, making the return on investment for creating convincing fake pages very high.
Mitigation and Defense Strategies
Enterprise security teams should treat this as a reminder to reinforce security awareness training, specifically highlighting the hallmarks of payment-themed phishing. Key indicators include generic greetings ("Dear Customer"), urgent calls to action, and links that do not match the official domain. Users should be trained to always navigate directly to a service's website by typing the URL or using a trusted bookmark, rather than clicking links in unsolicited emails.
For consumers, enabling multi-factor authentication (MFA) on streaming and other critical accounts is the most effective technical barrier. Even if credentials are stolen, MFA prevents account takeover. Email providers and security software are increasingly effective at filtering such messages, but zero-day phishing sites often slip through for a critical window of time.
Looking forward, security analysts predict that as subscription-based models proliferate across industries—from software to fitness—this specific phishing template will be adapted to target other services. The playbook is proven: exploit the customer's fear of losing access to a valued service. Proactive threat hunting and sharing of Indicators of Compromise (IOCs), such as phishing domain URLs and sending IP addresses, among security vendors and CERTs, are crucial to disrupting these campaigns at scale. The Netflix phishing wave is not just a consumer threat; it is a case study in the potent combination of social engineering and brand abuse that continues to challenge the cybersecurity ecosystem.
Comentarios 0
Comentando como:
¡Únete a la conversación!
Sé el primero en compartir tu opinión sobre este artículo.
¡Inicia la conversación!
Sé el primero en comentar este artículo.