The cybersecurity landscape is witnessing an alarming resurgence of USB-based malware attacks, with 2025 marking a significant uptick in sophisticated hardware-based threats. Security analysts report that modified USB devices and compromised public charging stations are being weaponized to bypass traditional security defenses, creating new challenges for organizations worldwide.
This revival of USB malware represents a strategic shift by threat actors who are exploiting the inherent trust users place in physical connections. Unlike network-based attacks that must penetrate firewalls and intrusion detection systems, USB malware operates at the hardware level, often evading conventional security software. The attacks leverage social engineering tactics, presenting as benign charging stations in airports, hotels, and public spaces, or as legitimate-looking storage devices left in strategic locations.
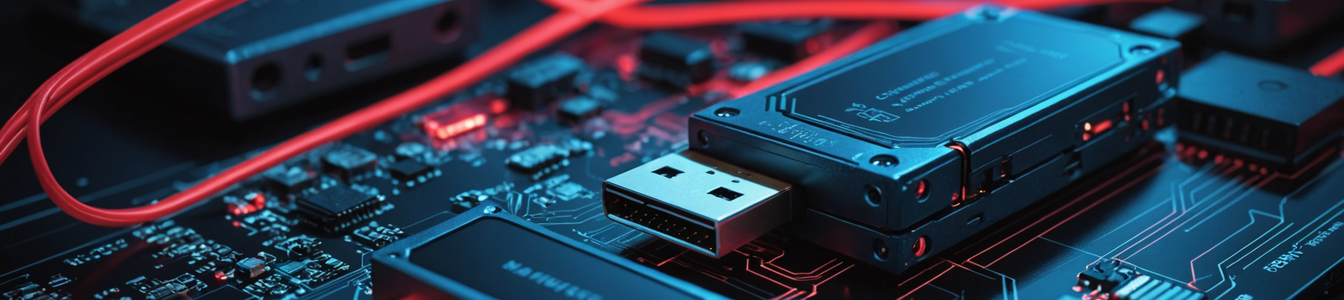
The technical sophistication of these attacks has evolved significantly. Modern USB malware can emulate multiple device types, including keyboards, network interfaces, and storage controllers, enabling complex attack sequences without user interaction. Some variants incorporate hardware-level modifications that make detection through software scanning nearly impossible. These devices can install persistent backdoors, exfiltrate sensitive data, or deploy ransomware payloads within seconds of connection.
Concurrently, the mobile threat landscape has expanded with fake banking applications and malicious APK files circulating through unofficial app stores and phishing campaigns. These mobile threats often work in tandem with USB-based attacks, creating comprehensive compromise chains that target both mobile and desktop environments.
Enterprise security teams are reporting increased incidents involving USB-based initial access vectors. The medium-level impact assessment reflects the targeted nature of these attacks, which often focus on specific organizations or individuals rather than widespread distribution. However, the potential consequences remain severe, including intellectual property theft, financial fraud, and operational disruption.
Detection challenges are compounded by the variety of attack methodologies. Some malicious USB devices use BadUSB techniques that reprogram microcontroller firmware, while others employ hardware keyloggers or data exfiltration tools. Public charging stations may incorporate data-siphoning capabilities alongside legitimate power delivery functions.
Defense strategies require a multi-layered approach. Technical controls should include USB port management solutions, device whitelisting, and endpoint detection systems capable of identifying anomalous USB behavior. Organizational policies must address the human factor through comprehensive security awareness training that emphasizes the risks of unknown USB devices and public charging infrastructure.
Advanced security measures include implementing USB condoms that block data transfer while allowing charging, deploying network segmentation to limit the lateral movement of compromised devices, and conducting regular security assessments of all physical access points. Some organizations are moving toward zero-trust architectures that treat all USB connections as potentially malicious until verified.
The convergence of hardware-based and mobile threats underscores the need for integrated security frameworks. Security professionals must coordinate defensive measures across physical, network, and application layers to effectively counter these evolving attack vectors. Regular penetration testing that includes social engineering scenarios involving USB devices can help identify vulnerabilities before malicious actors exploit them.
As the threat landscape continues to evolve, the cybersecurity community must maintain vigilance against these physical attack vectors. The resurgence of USB malware serves as a reminder that security strategies must address both digital and physical threats in an increasingly interconnected world.
Comentarios 0
Comentando como:
¡Únete a la conversación!
Sé el primero en compartir tu opinión sobre este artículo.
¡Inicia la conversación!
Sé el primero en comentar este artículo.