The cryptocurrency industry is facing a critical deadline to address the threat posed by quantum computing, with analysts warning that Bitcoin's value could plummet below $50,000 by 2028 if security u...


The cryptocurrency industry is facing a critical deadline to address the threat posed by quantum computing, with analysts warning that Bitcoin's value could plummet below $50,000 by 2028 if security u...

Two significant but underreported consumer security developments are converging, highlighting evolving digital risks. Security researchers have identified a novel attack vector where threat actors upl...
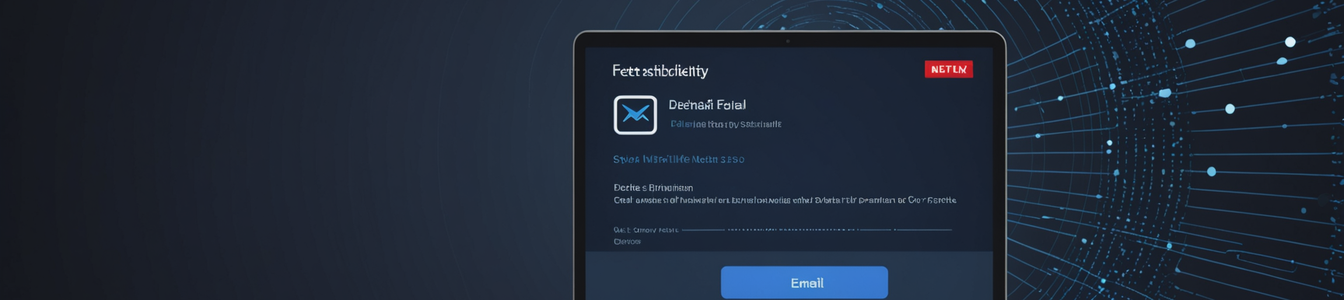
A sophisticated phishing campaign is targeting Netflix subscribers globally with convincing fake emails claiming payment failures and imminent account cancellation. The campaign, which has been partic...

Major cryptocurrency exchanges are undergoing a fundamental transformation, expanding from simple trading platforms into complex, multi-service financial ecosystems. Gemini has launched regulated pred...

Major cloud providers are accelerating partnerships with public institutions and educational organizations worldwide to promote AI and cloud literacy, raising significant cybersecurity and market conc...
A series of recent incidents reveals systemic weaknesses in audit and regulatory oversight that have significant implications for cybersecurity governance. The forced resignation of a PwC partner in S...

A wave of structural governance reforms is reshaping corporate oversight, with significant implications for cybersecurity and enterprise risk management. The independent board of Ben & Jerry's is unde...

The crypto and cybersecurity industries are mounting a coordinated defense of financial privacy tools in response to aggressive regulatory actions, most notably the recent prosecution of Samourai Wall...

India's Unique Identification Authority (UIDAI) has formalized face authentication as a new verification modality within its massive Aadhaar digital identity system, marking a significant regulatory e...

Recent announcements of prestigious partner awards from AWS, including DoiT's MSP designation and AI/R's Compass UOL being named Consulting Partner of the Year for LATAM, highlight a strategic consoli...
The impending shift to 23-hour, five-day-a-week trading for U.S. stocks and ETFs, as signaled by Nasdaq, represents a paradigm shift for financial sector Security Operations (SecOps). This move, drive...
The geopolitical competition for control over next-generation sensing technologies is accelerating, with significant developments in both acoustic micro-sensors and automotive radar systems. A breakth...

Merriam-Webster's selection of 'slop' as 2025's Word of the Year marks a cultural inflection point, recognizing the pervasive flood of low-quality, AI-generated content. This phenomenon extends beyond...

A coordinated yet unannounced wave of regulatory shifts by the EU, UK, US, and India is fundamentally reshaping the global compliance landscape for critical industries. The EU is advancing new carbon-...
A new wave of cybersecurity threats is exploiting fundamental smartphone functionalities that users and enterprises often overlook. Security researchers are highlighting vulnerabilities in core system...

A global examination of fiscal governance reveals stark contrasts between successful transparency initiatives and systemic failures in fund oversight. Nigeria's World Bank-praised SFTAS program demons...

The geopolitical landscape for technology and cybersecurity is undergoing a dramatic realignment. In a significant move signaling deteriorating international cooperation, the United States has suspend...

Security researchers have uncovered a sophisticated, large-scale phishing campaign targeting businesses globally by impersonating trusted collaboration platforms Microsoft SharePoint and e-signature s...

A recent hoax bomb threat targeting Rajiv Gandhi International Airport (RGIA) in Hyderabad has exposed how modern threat actors are leveraging legitimate privacy tools like Tor and VPNs to anonymize a...
Millions of consumers face a critical deadline this week to file claims in the massive AT&T data breach settlement, which could provide compensation of up to $7,500 for affected individuals. Simultane...