A new wave of strategic, pre-integrated partnerships between chipmakers, AI software firms, and OEMs is fundamentally altering the security architecture of the smart home ecosystem. While collaboratio...


A new wave of strategic, pre-integrated partnerships between chipmakers, AI software firms, and OEMs is fundamentally altering the security architecture of the smart home ecosystem. While collaboratio...

India's aggressive push towards digital tax compliance, including the upcoming GST 2.0 framework and state-level VAT amendments, is creating a vast new attack surface for cybercriminals. While designe...
The smartphone industry has become a primary battleground for geopolitical tensions, with Taiwan's arrest warrant for OnePlus CEO Pete Lau over alleged illegal hiring practices representing just one f...
Pakistan's recent memorandum of understanding with World Liberty Financial, a firm connected to the Trump family's cryptocurrency ventures, to explore using its USD1 stablecoin for cross-border paymen...

Governments worldwide are accelerating legislative efforts to address the legal vacuum surrounding AI-generated content and copyright infringement. The UK is proposing a significant 'reset' of copyrig...

With the December 30, 2024 deadline for the EU's Markets in Crypto-Assets Regulation (MiCAR) fast approaching, a two-tiered landscape is emerging with significant cybersecurity implications. While est...
A growing movement of technically proficient home users is taking network security into their own hands, building custom firewall solutions to combat pervasive data exfiltration from commercial IoT de...

A new generation of ambient, non-wearable health IoT devices is moving monitoring into the most private spaces—the bathroom and bedroom—creating continuous, passive streams of intimate bodily data...
The geopolitical battle over AI chip supremacy has entered a dangerously ambiguous phase, creating unprecedented supply chain security risks. Conflicting signals emerge as the US Commerce Department r...

Two recent incidents involving European critical infrastructure highlight the complex challenges facing national security teams. In Greece, a nationwide aviation blackout that grounded flights and spa...
The first Patch Tuesday of 2026 has been marked by two high-severity vulnerabilities requiring urgent enterprise attention. Microsoft has addressed a zero-day flaw in its Windows ecosystem that is alr...
A significant insider threat incident has resulted in the leak of personal and professional details of approximately 4,500 U.S. Immigration and Customs Enforcement (ICE) and Border Patrol agents. The ...
Security researchers have uncovered a previously unknown and highly sophisticated Linux malware framework dubbed 'VoidLink,' designed explicitly for stealthy, long-term compromise of cloud and contain...
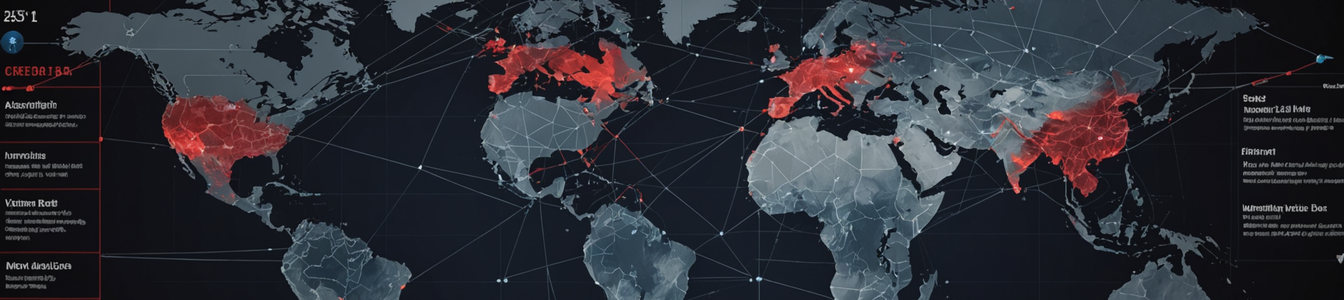
A convergence of geopolitical unrest and institutional crises is creating unprecedented indirect pressure on Security Operations Centers (SOCs) worldwide. As violent protests escalate in Iran and Bang...

The aggressive pursuit of digital financial rewards—from credit card churning and manufactured spending to exploiting sign-up bonuses and cashback loopholes—is attracting unprecedented scrutiny fr...

A dangerous disconnect exists between consumer self-perceived cybersecurity awareness and their actual vulnerability, particularly during high-pressure retail events like holiday sales. While most con...

The AI landscape is undergoing a seismic shift as strategic partnerships between tech giants reshape market dynamics and create new security paradigms. Apple's reported decision to integrate Google's ...

Aggressive promotional campaigns by major VPN providers, including discounts of up to 78% on multi-year plans, are directly capitalizing on the fragmented global streaming market. While marketed as to...

A wave of environmental, safety, and financial audits across Asia is revealing a disturbing pattern: compliance checks are uncovering systemic failures where physical infrastructure weaknesses interse...

Within hours of a data breach disclosure, a specialized legal ecosystem springs into action. A recent flurry of public announcements from law firms like Lynch Carpenter, launching investigations into ...