Recent geopolitical tensions involving US sanctions against Venezuela and Russia are creating unexpected cybersecurity vulnerabilities in international sporting events and their associated supply chai...


Recent geopolitical tensions involving US sanctions against Venezuela and Russia are creating unexpected cybersecurity vulnerabilities in international sporting events and their associated supply chai...

The M. Chinnaswamy Stadium in Bengaluru has received conditional approval to host IPL and international cricket matches, pending a final safety review that will determine its maximum crowd capacity. T...

A wave of state-level blockchain and cryptocurrency initiatives is forcing governments and central banks to rapidly adapt their security and regulatory postures. From the Philippines' adoption of a na...

India's critical infrastructure presents a cybersecurity paradox. While power distribution companies (discoms) report their first profits in years—₹2,701 crore in FY25—signaling financial and op...
Google's recent introduction of a feature allowing Gmail users to change their displayed sender name and email address is being actively exploited by cybercriminals to create highly convincing phishin...

In a significant shift toward proactive data privacy, California has implemented new legislation that fundamentally changes how residents can manage their digital footprint. The law, known informally ...

The U.S. cryptocurrency regulatory landscape is experiencing significant turbulence, marked by stalled legislation, emerging protections for software developers, and escalating tensions between indust...
A new class of security threats is emerging from seemingly innocuous file-sharing utilities that enable continuous, background synchronization between mobile devices and PCs. Tools like Syncthing and ...
Ahead of India's Union Budget 2026, intense sectoral lobbying is shaping the nation's cybersecurity investment landscape. Healthcare leaders, capital market investors, and trade policy experts are adv...

The decision by India's National Medical Commission (NMC) to revoke permission for the MBBS course at Mata Vaishno Devi College in Jammu & Kashmir has escalated into a significant governance crisis, h...

A stark analysis reveals that approximately 80% of cryptocurrency and DeFi projects that suffer a major security breach never fully recover, despite a growing ecosystem of recovery tools and insurance...
Large-scale institutional deployments of tablets, particularly in education, are creating a persistent and growing cybersecurity threat as these devices age beyond their supported lifecycle. While ini...
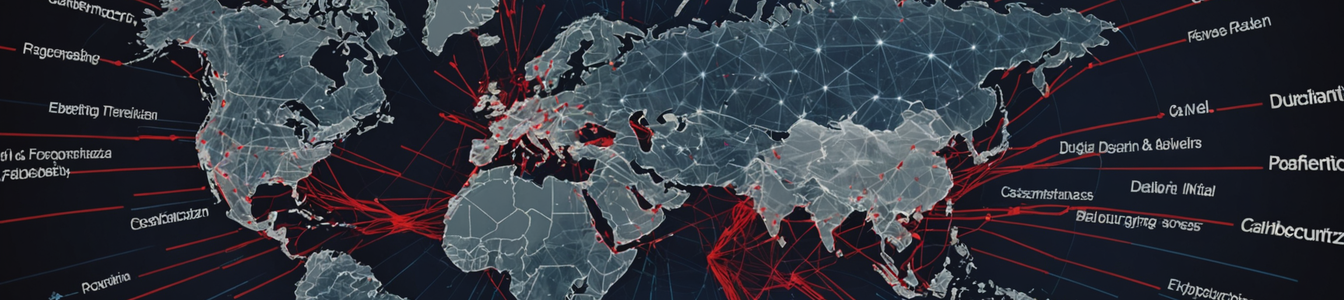
A sophisticated cyber espionage campaign has been uncovered, revealing how state-linked threat actors are weaponizing real-world geopolitical crises to enhance the effectiveness of their phishing oper...

The global AI landscape is being violently reshaped by a dual-front conflict: high-stakes intellectual property litigation and geopolitical battles over critical hardware. Elon Musk's unprecedented $1...

The IoT security landscape is undergoing a fundamental shift as sensor technology moves from environmental monitoring to direct personal chemical analysis. A new generation of devices, exemplified by ...

The rapid integration of AI into educational systems, exemplified by Google's new textbook conversion tool and Microsoft's shift toward AI-driven learning platforms, is creating unprecedented security...

Recent tragedies, including a fatal Swiss bar fire where staff lacked basic safety training, and systemic emergency response failures in India, reveal a dangerous pattern of neglected workforce prepar...

Simultaneous but contradictory policy shifts in the United States and India regarding electric vehicles (EVs) and automotive regulation are exposing significant security and safety vulnerabilities in ...

The VPN landscape is undergoing a fundamental architectural shift, moving beyond traditional client-server models toward more dynamic, identity-aware mesh networks. While WireGuard has revolutionized ...

The proliferation of low-cost, app-controlled IoT devices is revolutionizing small-scale agriculture, promising increased efficiency and yield. However, this rapid democratization of agricultural tech...